Org-mode and wide TaskJuggler HTML export
By default, when using the TaskJuggler exporting function in Org-mode, it will produce a web page that is too narrow by today’s standards:
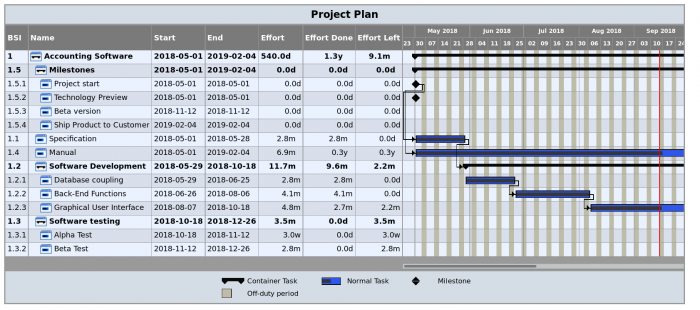
(Notice the scrollbar underneath the GANTT plot.)
The solution is to put a tweak in your emacs init file that adds columns ... { width 1000 } to the TaskJuggler output.
(setq org-taskjuggler-default-reports
'("textreport report \"Plan\" {
formats html
header '== %title =='
center -8<-
[#Plan Plan] | [#Resource_Allocation Resource Allocation]
----
=== Plan ===
<[report id=\"plan\"]>
----
=== Resource Allocation ===
<[report id=\"resourceGraph\"]>
->8-
}
# A traditional Gantt chart with a project overview.
taskreport plan \"\" {
headline \"Project Plan\"
columns bsi, name, start, end, effort, effortdone, effortleft, chart { width 1000 }
loadunit shortauto
hideresource 1
}
# A graph showing resource allocation. It identifies whether each
# resource is under- or over-allocated for.
resourcereport resourceGraph \"\" {
headline \"Resource Allocation Graph\"
columns no, name, effort, weekly { width 1000 }
loadunit shortauto
hidetask ~(isleaf() & isleaf_())
sorttasks plan.start.up
}")
)
Also, some other tweaks that I found useful:
(setq org-taskjuggler-default-project-duration 999) (setq org-taskjuggler-valid-task-attributes '(account start note duration endbuffer endcredit end flags journalentry length limits maxend maxstart minend minstart period reference responsible scheduling startbuffer startcredit statusnote chargeset charge booking))
The first sets the default project duration that I couldn’t seem to set in the org file itself. The second makes it possible to add booking clauses to tasks (so you can define those inside your org files).
Finally, I also found it useful to tweak the columns in the GANTT chart. I added the effortdone and effortleft fields, which are visible in the above screenshot.