Transferring 4K video files from a Sony action cam (FDR-X3000) to an iPhone
When using Sony action cameras that are capable of recording in the XAVC-S format (e.g. FDR-X3000), especially in 4K, it is not immediately obvious how to transfer these files to an iPhone.
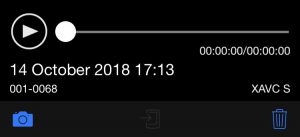
When using the Sony PlayMemories app, the option to transfer the files to the iPhone is grayed out (the middle icon in the below toolbar):
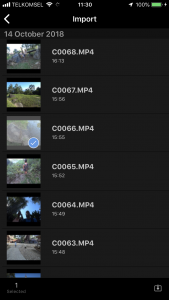
The solution is to use a different app, namely the Sony “Action Cam” app. In this app, click “Import”:
Then you will find that if you select a file, it will now even import 4K:
Note: in this approach the downloaded file will be downscaled, and you won’t have the full 4K video on your iPhone. However, this downscaled video can be useful for sharing on social media.
If you want full quality 4K transferred to the iPhone, you have this remaining option (besides using a PC, of course), which is to use the Leef dongle that has a micro SD card reader for iPhone. (If you have a recent iPhone that supports 4K.)
Note that the Leef will also work for A7 cameras, but it only has a micro SD card slot, so you’ll need an adapter.